Need to generate MD5 hashes quickly? Our MD5 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
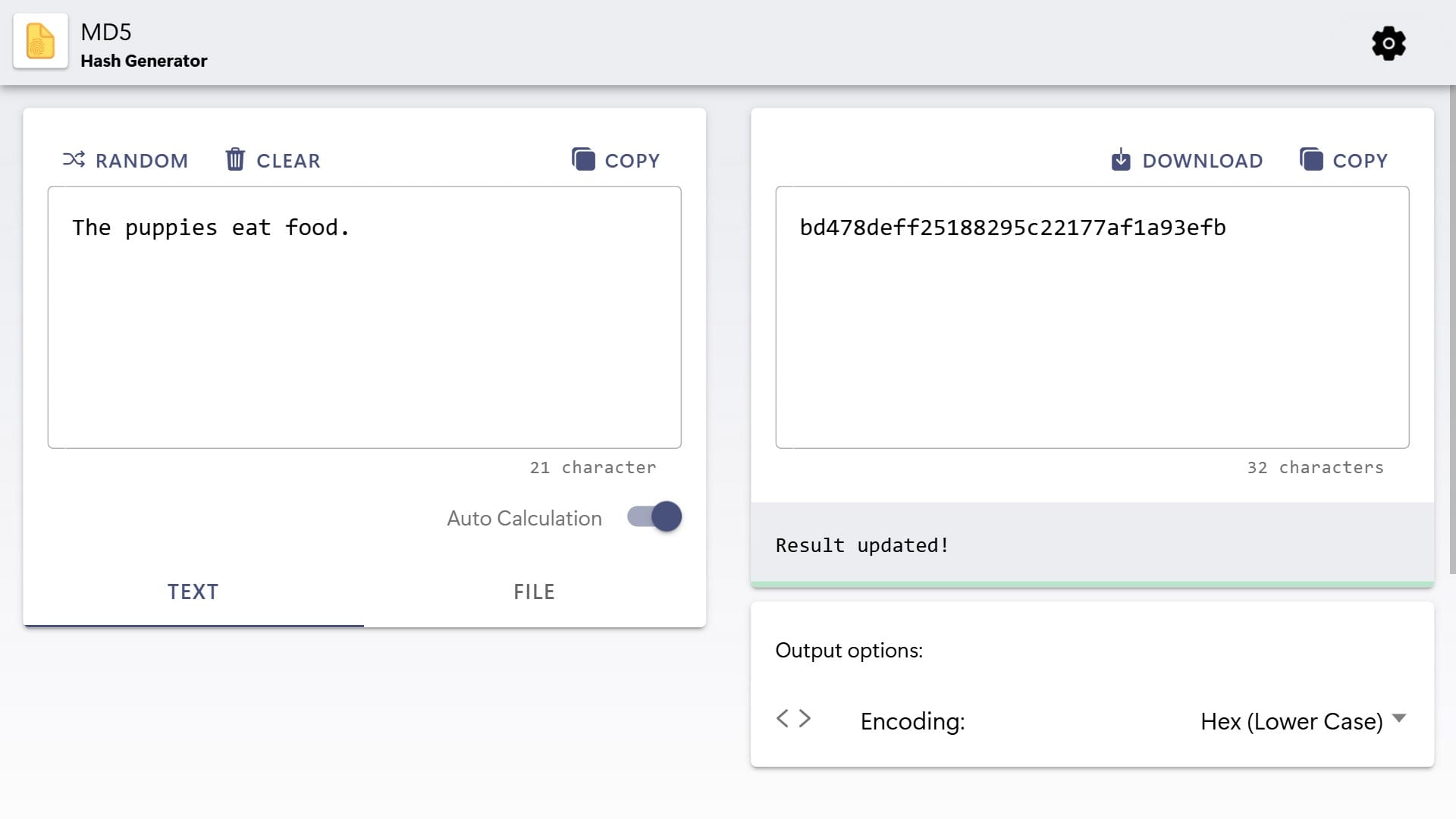
MD5 hashes act like digital fingerprints to verify information. We will explain how they work and the steps to use them effectively. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
What is MD5?
MD5, short for Message Digest Algorithm 5, is a cryptographic hash function that generates fixed 128-bit codes to verify data integrity. Authored by cryptographer Ronald Rivest[1] in 1991, it processes data of any length documents, text strings, or digital files and transforms them into distinct alphanumeric sequences.
Initially, MD5 was appreciated for its speed and simple design. Even though newer systems are now available, they are still recognized as an important method for generating unique digital fingerprints. Rivest's work laid the groundwork for basic principles that are still important in discussions about data security today.
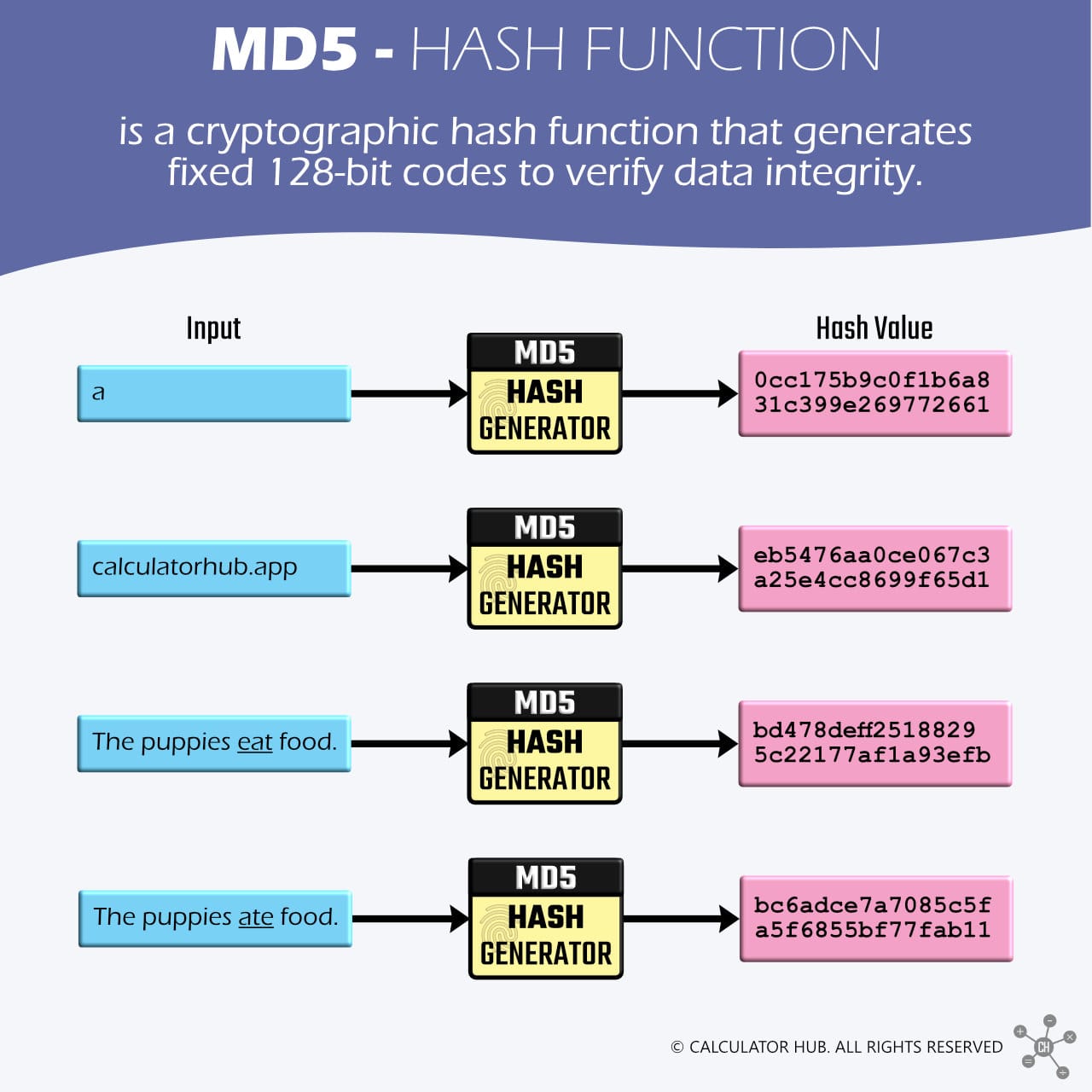
Key Features of MD5
Here are the key features of the MD5 cryptographic hash function.
- Fixed 128-Bit Output: No matter how big or small your input is, MD5 always spits out a 128-bit hash (like a fixed-length ID tag for data).
- One-Way Function: Hashes cannot be reversed to reveal the original input (no practical method exists).
- Input Sensitivity: Changing even a single character or bit in the input will completely alter the hash, a phenomenon known as the "avalanche effect."[2]
- Built for Speed: MD5 works lightning-fast, which made it popular for tasks like checking file integrity or quick data comparisons.
Examples
Here are some real-life examples of how developers and systems have utilized MD5 in various situations.
Software Distributions
Linux OS downloads often include MD5 checksums so users can confirm ISO files match the original. Here is an example of MD5 checksums for Ubuntu ISO images that you can find at https://old-releases.ubuntu.com/releases/bionic/MD5SUMS.
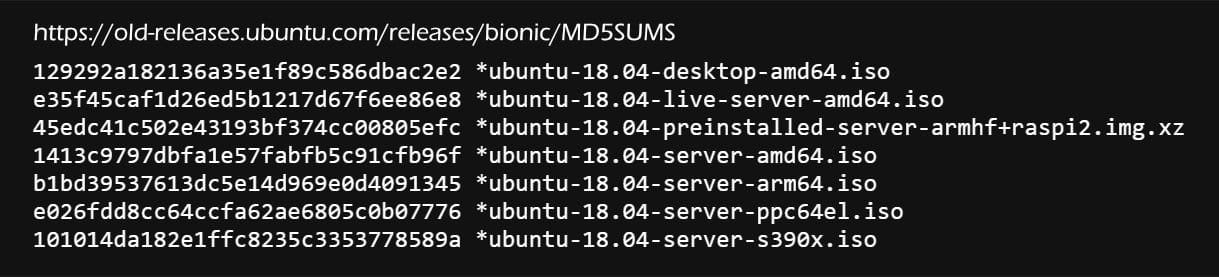
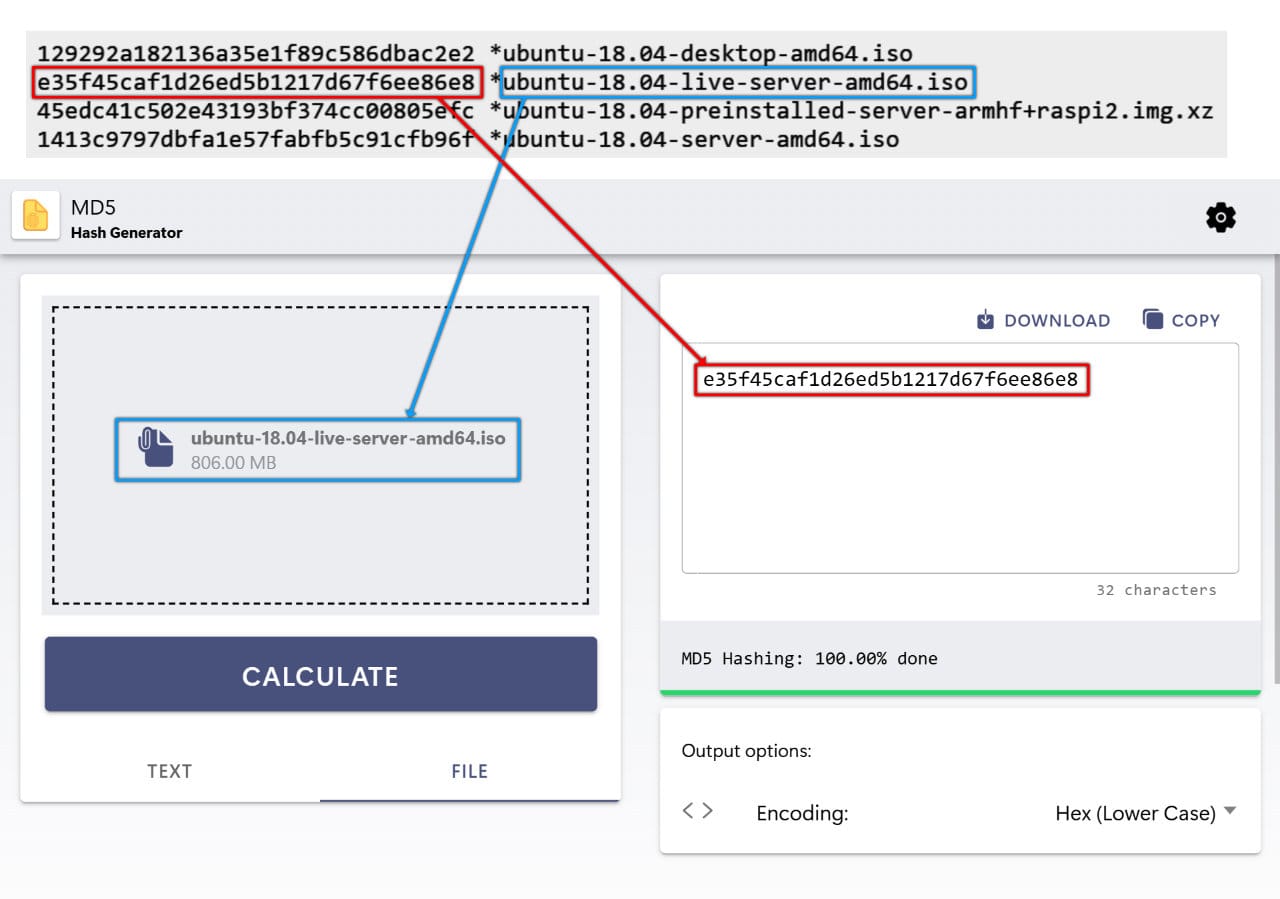
To demonstrate how to use our MD5 Hash Generator, I will download the ISO file named "ubuntu-18.04-live-server-amd64.iso" and verify that it has downloaded correctly.
First, I will navigate to the File tab, select the downloaded ISO file, and click "Calculate" to generate its hash value. This process may take a few minutes, depending on the speed of your computer.
Once the calculation is complete, I will compare the hash result from our generator with the MD5 checksum provided on the official website. As you can see, the hash values match.
Cloud Storage
Services like OneDrive, Google Drive, or Dropbox use MD5 to find duplicate files and save server space.
Corporate Data Transfers
Teams use MD5 to quickly check if large files (like databases) arrive intact after network transfers.
How MD5 Works
The primary goal of MD5 is to take input data of any size and produce a fixed-size 128-bit hash value, which is widely used in checksums and data integrity verification.
Here’s its step-by-step process of how the MD5 (Message-Digest Algorithm 5) works, based on the RFC 1321 document[3]:
Step 1. Padding the Input
The input is split into 512-bit blocks. If the message isn’t long enough, it gets padded:
- A single ‘1’ bit is added first.
- Then, ‘0’ bits fill the space until the total length is 64 bits shorter than the next 512-bit multiple.
- The final 64 bits store the original message’s length.
Step 2. Setting Up Registers
Four 32-bit registers (A, B, C, D) start with fixed values defined in the MD5 standard.
A = 0x67452301B = 0xEFCDAB89C = 0x98BADCFED = 0x10325476
Step 3. Block Processing
Each 512-bit block undergoes four rounds (16 operations each):
- Uses basic logic operations (AND, OR, NOT, XOR).
- Applies bit rotations and modular addition (ignoring overflows beyond 32 bits).
- Mixes data with predefined constants to amplify small input changes.
Step 4. Updating State
After each block, the results from the four rounds update the A/B/C/D registers.
Step 5. Final Hash
Once all blocks are processed, the 32-bit values from A, B, C, and D are combined into the 128-bit hash.
FAQs
1. What are the common use cases of the MD5 Hash Generator?
MD5 hash generator is widely used for everyday tasks in verification workflows. Here’s where they’re most often applied:
- Checking File Integrity
- Mainly used to verify files haven’t changed during downloads or transfers.
- Users compare the source’s MD5 hash with their file’s hash to spot changes or corruption.
- Spotting File Tampering
- Ensures files stay original by detecting edits.
- Software teams sometimes share MD5 hashes with downloads to prove files aren’t altered post-release.
- Quick Checksums
- Creates short “data fingerprints” to confirm backups or systems haven’t lost/damaged files.
- Basic Document Verification
- Rarely used today, but older systems might still use MD5 for simple document signatures (not recommended for security).
2. Why do people still use MD5 if it’s outdated?
MD5 sticks around for simple jobs because it’s fast and works everywhere. It gives the same 128-bit hash for any file size in seconds, and it’s built into tons of tools and older systems. So it’s easy to use for basic tasks where security isn’t a priority.
3. When should I use MD5?
Use it for quick checks, like verifying downloads didn’t get corrupted or making sure files haven’t accidentally changed. It works best for internal tasks where speed matters more than security (e.g., generating checksums for non-sensitive data).
4. Is MD5 okay to use today?
Avoid it for anything security-related. Modern systems use stronger algorithms like SHA-256 or SHA-3, which are designed to resist today’s hacking methods. MD5 is only “safe” for non-critical jobs like checking file typos.








