Need to generate checksums or hashes quickly? This tool lets you create them by typing text or uploading files using methods like MD5 and SHA-1. It’s a straightforward way to check data accuracy or confirm files haven’t been altered.
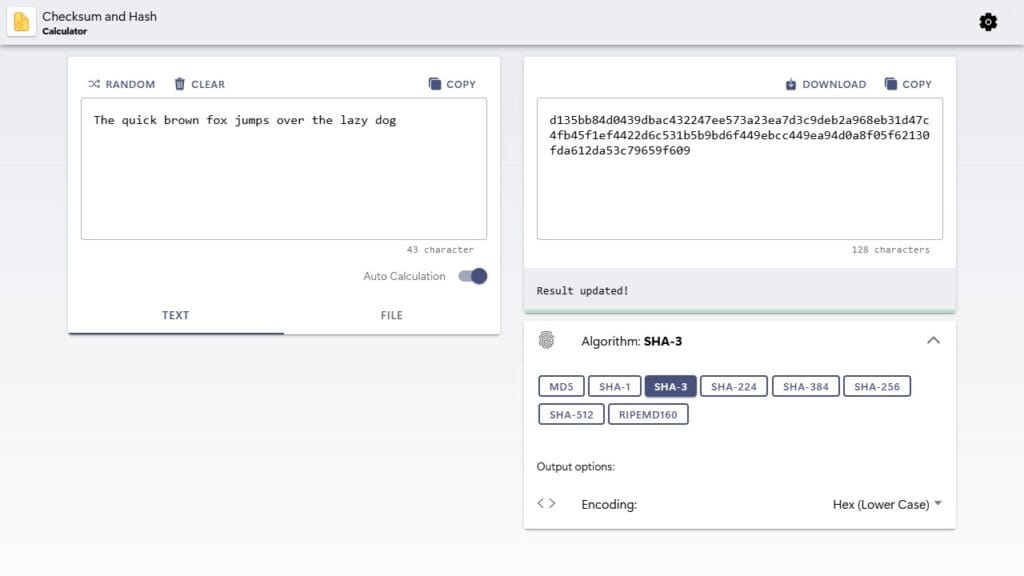
Checksums and hashes act like digital fingerprints to verify information. We will explain how they work and the steps to use them effectively. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
Let’s get started by understanding the key definitions. Checksums and hashes work like digital fingerprints that confirm data hasn’t been changed.
What is a checksum?
A checksum is a simpler tool for spotting errors. They use a quick math formula to create a short code from data. If anything in the data shifts, even slightly, the checksum changes. This makes them handy for catching mistakes in downloads or file transfers.
What is a hash?
A hash does something similar to a checksum but adds extra security layers. They turn data of any size into a fixed code, often used to lock down passwords or check if files are unaltered. Popular methods like SHA-256 or MD5 make hashes nearly impossible to reverse or duplicate.
The key difference? Checksums flag basic errors, while hashes handle tougher jobs like verifying authenticity. Hashes are built to avoid “collisions”, where two different inputs accidentally create the same code, making them critical for security. Both tools quietly protect data reliability, whether confirming a file’s safety or ensuring a message arrives intact.
Hash Algorithms
Here's a table that compares popular cryptographic hash algorithms, including their bit lengths and primary applications.
| Algorithm | Bit Length (Hex Characters) | Use Cases |
|---|---|---|
| MD5 | 128 bits32 hex | Checksum verification, legacy applications (considered insecure) |
| SHA-1 | 160 bits40 hex | Digital signatures, SSL/TLS (deprecated due to collision vulnerabilities) |
| RIPEMD-160 | 160 bits40 hex | Blockchain addresses, digital signatures, and checksum verification |
| SHA-224 | 224 bits56 hex | Cryptographic integrity verification, security applications |
| SHA-256 | 256 bits64 hex | Blockchain security, digital signatures, and password hashing |
| SHA-384 | 384 bits96 hex | Financial transactions, SSL/TLS encryption, and secure authentication |
| SHA-512 | 512 bits128 hex | High-security applications, encryption, and password hashing |
| SHA3-224 | 224 bits56 hex | Secure cryptographic hashing, an alternative to SHA-2 |
| SHA3-256 | 256 bits64 hex | Blockchain security, digital signatures, and password hashing |
| SHA3-384 | 384 bits96 hex | Cryptographic security, digital signatures, and authentication |
| SHA3-512 | 512 bits128 hex | Maximum security applications, encryption, and data integrity |
FAQs
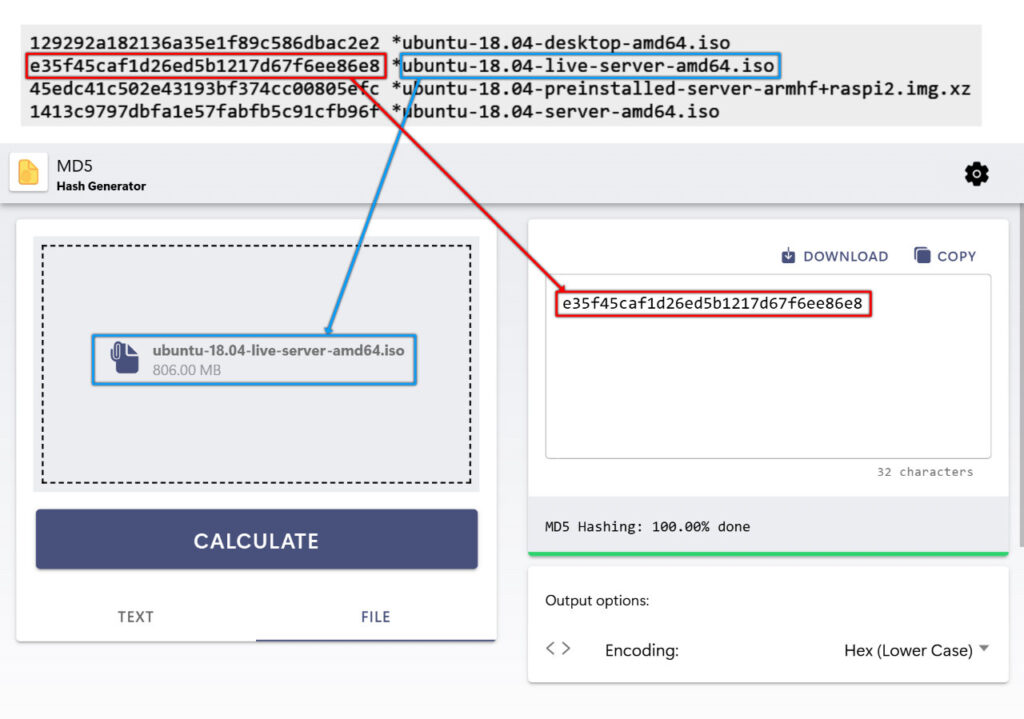
1. How can I verify a file’s integrity using a hash generator?
To check a file's integrity, users generate its hash value using a hash generator and compare it with the original published hash. If the values match, the file has not been altered.
Here are the detailed steps:
- On the main app page, select "File" from the menu tab.
- Click on the "Select a File" area to open the Open dialog box.
- Choose the file for which you want to generate a hash.
- Click "Calculate" to begin generating the hash.
- Wait until the progress reaches 100%.
- The output hash will then appear in the result box.
- You can now compare the generated hash with the hash provided on the download page.
2. Why is MD5 considered weak for cryptographic security?
MD5, once widely used, is now deprecated due to its vulnerability to collision attacks, where two different inputs produce the same hash. Modern applications use SHA-2 or SHA-3 for stronger security.
3. Why are SHA-256 and SHA-512 preferred over older hash functions?
SHA-256 and SHA-512 offer stronger security and collision resistance, making them ideal for blockchain technology, digital signatures, encrypted communications, and financial data protection.








