Need to generate SHA-512 hashes quickly? Our SHA-512 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
SHA-512 is one of the most secure cryptographic hash functions in the SHA-2 family, producing a 512-bit hash for maximum resistance against cryptographic attacks. It is widely used in data integrity verification, password hashing, SSL/TLS encryption, digital signatures, and blockchain security. To help you learn more about SHA-512, we will explain the basic terms, provide examples, and answer common questions to enhance your understanding.
Definitions
What is SHA-512?
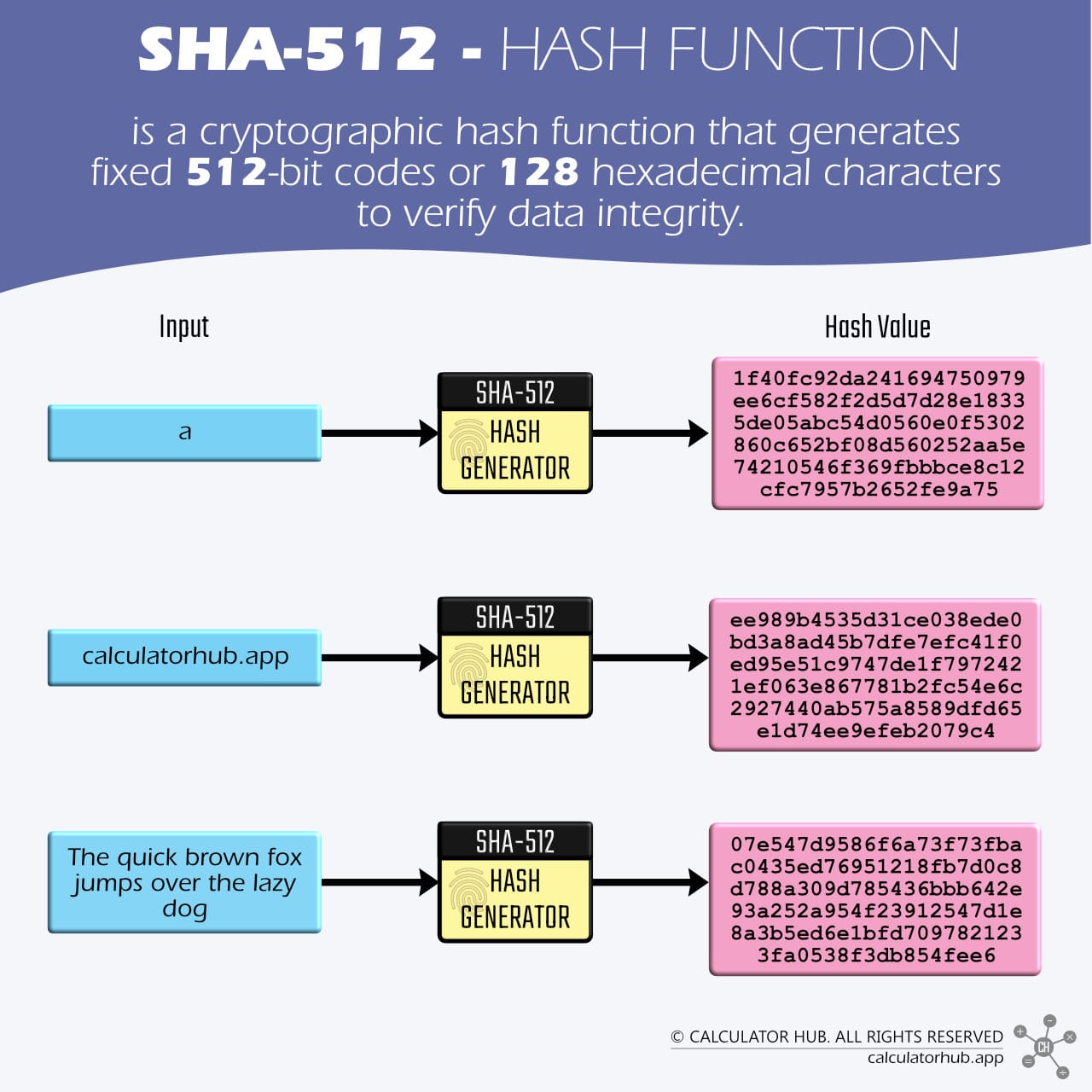
SHA-512 is the powerhouse of the SHA-2 family, creating an ultra-secure 512-bit "fingerprint" of your data. Developed by the NSA and standardized by NIST in 2001[1], it works like a digital blender - turning files, passwords, or documents into unique, unreadable hashes that can't be reversed. While SHA-256 and SHA-384 are secure, SHA-512 offers even stronger protection thanks to its longer hash length.
Its massive 512-bit output makes it extremely resistant to hacking attempts, ensuring your data stays protected for decades. While it requires slightly more computing power than its smaller siblings, that extra strength makes it ideal for protecting high-value information where absolute security matters most.
Key Features
Here are the key features of the SHA-512 cryptographic hash function.
- Fixed 512-Bit Output: Regardless of input size, SHA-512 always produces a 512-bit hash, offering stronger security than SHA-256 and SHA-384.
- Strong Collision Resistance: Its larger hash size significantly reduces the risk of collisions, making it highly secure for cryptographic applications.
- One-Way Function: It is computationally infeasible to reverse the hash and retrieve the original input, ensuring strong data protection.
- Avalanche Effect: Even the smallest change in the input completely alters the hash, reinforcing data integrity and security.
- Optimized for High-Security Applications: Widely used in TLS/SSL encryption, digital signatures, blockchain technology, financial security, and secure password hashing, SHA-512 provides long-term protection against evolving cyber threats.
- Block-Based Processing: SHA-512 processes data in 1024-bit blocks, executing 80 rounds of complex transformations including bitwise operations, modular additions, and logical functions to enhance security.
Examples
Here’s a table of text samples along with their corresponding SHA-512 hash values:
| Text Input | SHA-512 Hash Output |
|---|---|
Apple | 393374ca4948ba5d30d24c45611a17a7f63ac98904dd17da4a8cdab2854a611daba24786a252d2d476a446cb476a5332bafb41b1409591683b6a5ce7680ba9e2 |
Banana | 6e5851a3b5c72e49f5a3ed405c1d93ad16b6b542846430e06037bbe8d47dab70a64b88374be2c229cb3152d4885ff822c42c122cd8112bce87b9e55c5da855d8 |
Blackberry | d8c4292aba4508b54902c33c1b1c69ad9d05159f555a13264b0ec6658f678085b9deadd54794b4aab4c7a26fbe91c4533513c26754f83b900d895be1b1190815 |
Cherry | 186752feafc28c0f3f14aaeb28651ebb6cc3a52d8c083f346850ec75fce9ab1099db1466bf0474d2d4ab00094ff4e582cbfec3688976a5eb3736c33cd504cb60 |
password | b109f3bbbc244eb82441917ed06d618b9008dd09b3befd1b5e07394c706a8bb980b1d7785e5976ec049b46df5f1326af5a2ea6d103fd07c95385ffab0cacbc86 |
The quick brown fox jumps over the lazy dog | 07e547d9586f6a73f73fbac0435ed76951218fb7d0c8d788a309d785436bbb642e93a252a954f23912547d1e8a3b5ed6e1bfd7097821233fa0538f3db854fee6 |
FAQs
1. Can SHA-512 be "decrypted"?
No, SHA-512 is a one-way hash function, meaning it cannot be reversed or decrypted. Unlike encryption algorithms that allow for decryption with a key, hash functions like SHA-512 only generate fixed-length outputs with no way to retrieve the original data.
2. Is SHA-512 safer than SHA-256?
Yes, the longer code makes it way tougher for hackers to fake matching hashes (collisions). SHA-512 offers greater resistance to collision attacks due to its longer hash length, making it harder for attackers to generate two different inputs with the same hash.
3. What are practical use cases for SHA-512?
SHA-512 is a powerful tool used to protect sensitive information across various fields. Here’s a simple breakdown of its key applications:
- Securing Website Connections: SHA-512 helps encrypt data (like passwords, payments, or personal details) during online interactions, ensuring safe communication between your browser and websites via TLS/SSL protocols.
- Digital Signatures & Certificate Authentication: It’s used in digital signatures to confirm files, emails, or software updates haven’t been altered. Think of it as a tamper-proof seal, organizations hash documents and sign them with a private key, letting others verify integrity with a public key.
- Blockchain & Crypto Security: In blockchain systems, SHA-512 secures transaction records and blocks, making them unchangeable. Some cryptocurrencies rely on it to validate transactions and safeguard digital assets from hacking.
- Storing Passwords Safely: While SHA-512 alone isn’t ideal for passwords (due to speed aiding hackers), it’s paired with slower algorithms like bcrypt or Argon2. This combo strengthens security by making password cracking time-consuming.
- High-Stakes Data Protection: Banks, governments, and financial institutions use SHA-512 to shield transactions, IDs, and sensitive records, meeting strict regulatory standards where top-tier security is non-negotiable.
- Checking File Integrity: Companies use SHA-512 to detect unauthorized changes in files or databases. By comparing hashes before and after storage, they ensure data remains untouched, critical for audits, logs, or forensic investigations.
4. How does SHA-512 differ from SHA-256?
While both SHA-512and SHA-256 belong to the SHA-2 family, they differ in hash length, processing structure, initialization values, and security strength. SHA-512 produces a 512-bit hash, whereas SHA-256 generates a 256-bit hash. SHA-512 also processes data in 1024-bit blocks with 80 rounds of transformations, offering greater resistance against cryptographic attacks








