Need to generate SHA-384 hashes quickly? Our SHA-384 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
SHA-384 is another member of the SHA-2 family, designed for enhanced cryptographic security with a 384-bit output, making it stronger than SHA-224 and SHA-256 while maintaining efficiency. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
What is SHA-384?
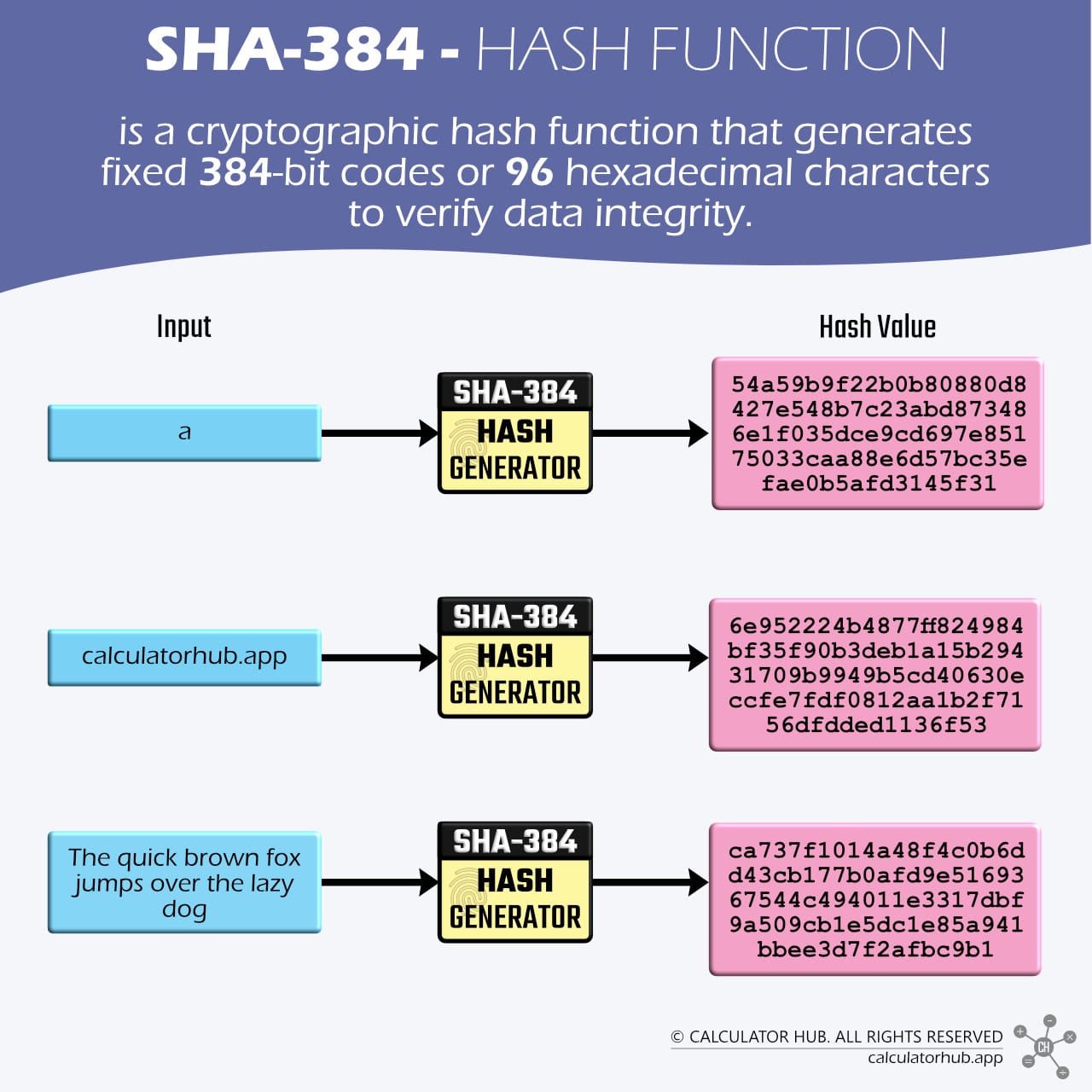
SHA-384 is a beefed-up version of SHA-256, part of the same SHA-2 family created by the NSA and NIST in 2001[1]. It scrambles data, including files, passwords, and transactions, into a unique 384-bit code, acting like a super-secure digital fingerprint. While it’s bigger than SHA-256, it’s still fast enough for modern systems.
Originally introduced for high-security applications, SHA-384 is widely used in TLS/SSL encryption, digital signatures, blockchain technology, and financial data protection. Its larger hash size makes it more resilient against cryptographic attacks while still operating efficiently within modern security frameworks.
Key Features
Here are the key features of the SHA-384 cryptographic hash function.
- Fixed 384-Bit Output: Regardless of input size, SHA-384 always produces a 384-bit hash, offering stronger security than SHA-256.
- Strong Collision Resistance: Its larger hash size significantly reduces the risk of collisions, making it highly secure for cryptographic applications.
- One-Way Function: It is computationally infeasible to reverse the hash and retrieve the original input, ensuring strong data protection.
- Avalanche Effect: Even the smallest change in the input completely alters the hash, reinforcing data integrity and security.
- Optimized for High-Security Applications: SHA-384 is widely used in TLS/SSL encryption, digital signatures, blockchain security, and financial cryptography.
- Block-Based Processing: It processes data in 1024-bit blocks, applying multiple transformations like bitwise shifts, modular additions, and logical functions to enhance security.
Examples
Here’s a table of text samples along with their corresponding SHA-384 hash values:
| Text Input | SHA-384 Hash Output |
|---|---|
Apple | ae75671328e39e45722556260cf82166547e8841ff3c2079c162fa4ffc5c80cd59fb80fa7da40fa12012f63a48d3ba2c |
Banana | 3c476b2ad9da9058df438bc49adbc7c8f0807753f9ad5b0e3196fc492b47846dea2e02a921aa3095e928a0409016cfbb |
Blackberry | 24defe8931e4a40f35cb0c83587a0862513c2ef7645f09b1dfd1a65fe597334a3b4abfc49a0e438ac10c8b8920163585 |
Cherry | 07926049a83b3a254cfbf5c9372e0ece3cb275f6fb93d09468f10dab4e898aa1db83d41264c1e913fc71537be5cea1a3 |
password | a8b64babd0aca91a59bdbb7761b421d4f2bb38280d3a75ba0f21f2bebc45583d446c598660c94ce680c47d19c30783a7 |
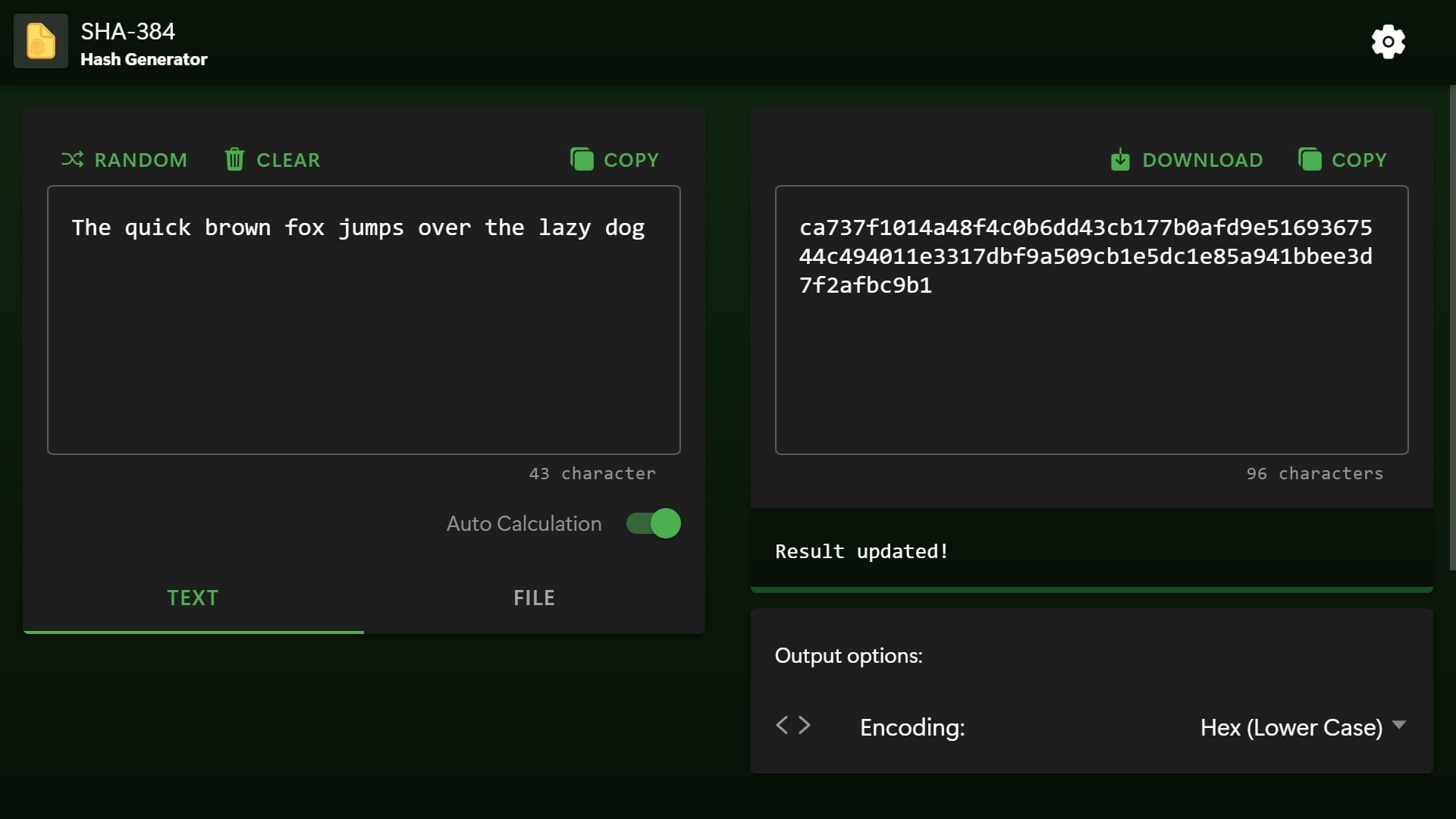
The quick brown fox jumps over the lazy dog | ca737f1014a48f4c0b6dd43cb177b0afd9e5169367544c494011e3317dbf9a509cb1e5dc1e85a941bbee3d7f2afbc9b1 |
FAQs
1. Can SHA-384 be "decrypted"?
No, SHA-384 is a one-way hash function, meaning it cannot be reversed or decrypted. Unlike encryption algorithms that allow for decryption with a key, hash functions like SHA-384 only generate fixed-length outputs with no way to retrieve the original data.
2. Is SHA-384 safer than SHA-256?
Yes, the longer code makes it way tougher for hackers to fake matching hashes (collisions). SHA-384 offers greater resistance to collision attacks due to its longer hash length, making it harder for attackers to generate two different inputs with the same hash.
3. What are practical use cases for SHA-384?
SHA-384 is widely used in cryptographic applications where high security and strong collision resistance are required. Here are some practical use cases for SHA-384:
- TLS/SSL Encryption: SHA-384 is commonly used in Transport Layer Security (TLS) to ensure secure communication between web browsers and servers, protecting sensitive data like passwords and financial transactions.
- Digital Signatures & Certificates: Many digital signature algorithms utilize SHA-384 for signing and verifying authenticity, ensuring documents, emails, and software updates remain untampered.
- Blockchain Security: Certain blockchain networks employ SHA-384 for data hashing, transaction validation, and block integrity, providing enhanced cryptographic protection against manipulation.
- Financial Data Protection: SHA-384 is used in banking and finance for secure data transmission, fraud prevention, and encryption of critical financial transactions, ensuring compliance with security standards.
- Secure Authentication Systems: It plays a role in authentication protocols, enhancing security in multi-factor authentication (MFA), password management systems, and access control mechanisms.
- Cryptographic Key Derivation: SHA-384 can be incorporated into key derivation functions (KDFs) like PBKDF2, helping create secure encryption keys used in encrypted storage and communication.
- Tamper-Proof Logs & Secure Archiving: Organizations use SHA-384 to ensure data integrity in logging systems, forensic recordkeeping, and document archiving, protecting against unauthorized alterations.
4. How does SHA-384 differ from SHA-256?
While both SHA-384 and SHA-256 belong to the SHA-2 family, they differ in hash length, processing structure, initialization values, and security strength. SHA-384 is essentially a higher-security variant of SHA-256, leveraging SHA-512’s robust processing structure while maintaining a more efficient output size. It is ideal for applications requiring enhanced security while balancing computational efficiency.








