Need to generate SHA-3 hashes quickly? Our SHA-3 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
SHA-3 is a completely different cryptographic hashing standard compared to SHA-2, designed to provide high-security levels while addressing potential vulnerabilities in older hash functions. Unlike SHA-2, SHA-3 is based on the Keccak algorithm[1], which operates using a sponge construction rather than the traditional Merkle–Damgård structure[2]. To help you learn more about SHA-3, we will explain the basic terms, provide examples, and answer common questions to enhance your understanding.
Definitions
What is SHA-3?
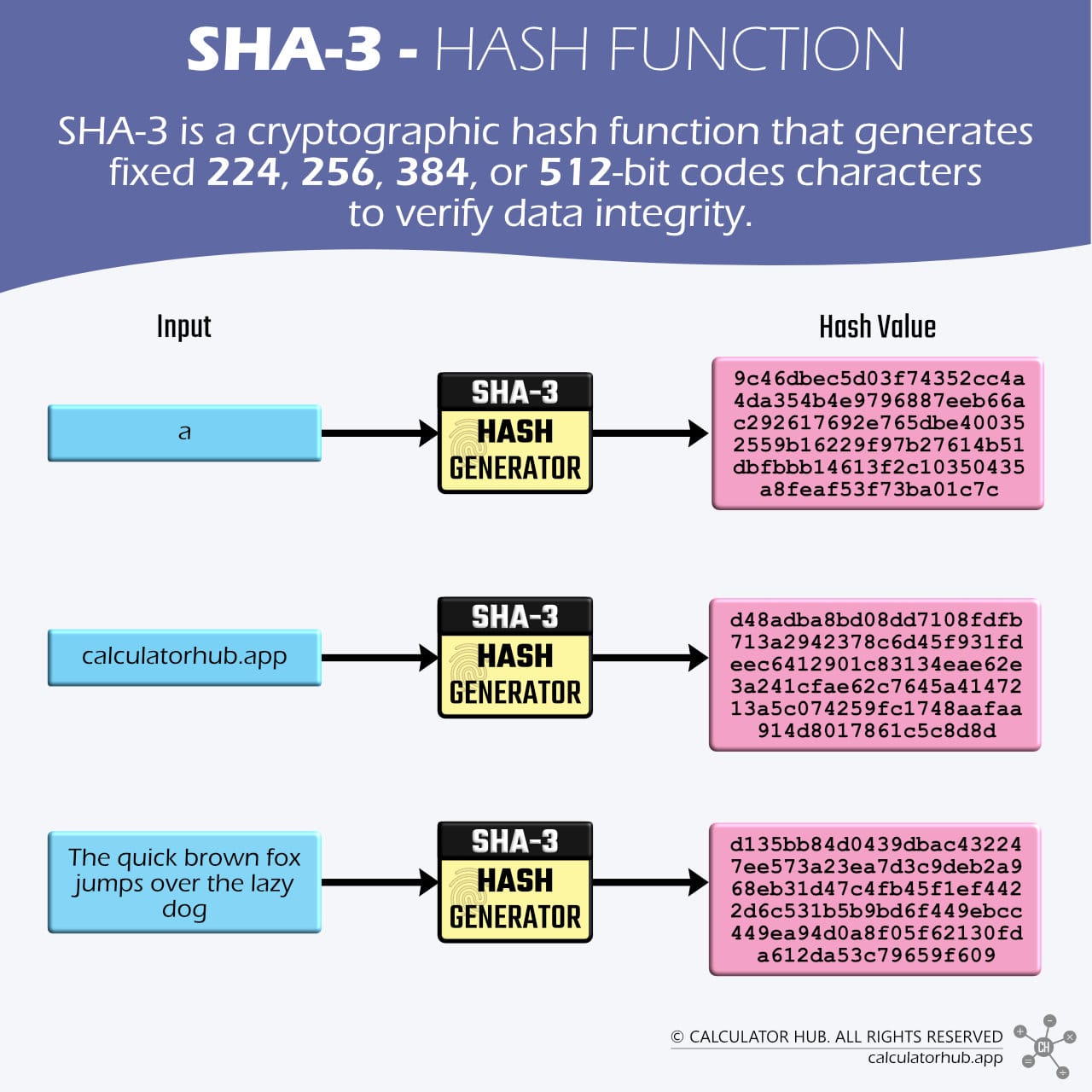
SHA-3 (Secure Hash Algorithm 3) is a cryptographic hash function designed to provide high security and resilience against emerging threats. SHA-3 is based on the Keccak algorithm, utilizing a unique sponge construction that enhances resistance to collision and preimage attacks.
Developed as a backup plan in case SHA-2 ever showed weaknesses, SHA-3 was approved by NIST in 2015[3]. It comes in four sizes (224, 256, 384, or 512-bit hashes) to match different security needs. While SHA-2 remains secure and widely used, SHA-3 is the go-to for cutting-edge systems like quantum-resistant encryption or ultra-secure government tech. Think of it as an optional upgrade: not mandatory, but invaluable for future-proofing sensitive data.
Key Features
SHA-3 works like a digital sponge, soaking up data, mixing it thoroughly, then squeezing out a unique hash. Unlike older methods (like SHA-2), this "sponge construction" avoids structural flaws, making it tougher to hack. Here’s why it stands out:
- Bulletproof Collision Resistance: It’s nearly impossible for two different files or inputs to produce the same hash, even if they’re almost identical.
- No Length-Extension Weaknesses: Unlike SHA-2, SHA-3 can’t be tricked into faking signatures or altering data by adding hidden content to inputs.
- Hardware-Friendly Speed: Runs efficiently on devices, from tiny IoT sensors to servers, making it ideal for encryption and real-time security checks.
- Future-Proof Design: While SHA-2 is still secure, SHA-3 eliminates theoretical risks in its structure, serving as a backup for high-stakes systems like blockchain, tamper-proof logs, or government-grade encryption.
- Flexible Security Levels: Choose from four hash sizes, including 224, 256, 384, or 512 bits, to match your needs (e.g., lighter security for apps, max strength for financial data).
SHA-3 produces hashes of different lengths depending on the variant used:
| SHA-3 Variant | Output Length (Bits) | Output Length (Hex Characters) |
|---|---|---|
| SHA3-224 | 224 bits | 56 hex characters |
| SHA3-256 | 256 bits | 64 hex characters |
| SHA3-384 | 384 bits | 96 hex characters |
| SHA3-512 | 512 bits | 128 hex characters |
Examples
Here’s a table of text samples along with their corresponding SHA3-512 hash values:
| Text Input | SHA3-512 Hash Output |
|---|---|
Apple | 21c686e444e77908dcca76e8d313036053d0919132fb1c711d190f0ebf63b3a74f548768b9887017ec6eb3e22d6bb13f71f72ed3df6cb5fca4e17fd6914b4a4a |
Banana | 5087be7cce205bbd0540f3b19a17f3bff2bea3ffea5f76f5e290f28356b85f811fe532edd49a3a2fdf1ef5a3e75a6e76059ef6caf79fa9706ad1cf5d2fdaafda |
Blackberry | d1d6ff04b70ef1953a485ec502369112206aaabb7c37319af58abf1099e68bd45014dc6a32b48b1478f9cdc0f3813b7888ebcb56f3a714c7b35ee5123a9fac32 |
Cherry | 6cf7bf3bb8cae056a615cfd226f3b76bbc48ec883dd50500313a009eb4a9f72d231c9727d46b8a1edb4602ed1c5833306f840bcde3232184d5c06c1338d6514c |
password | a6818b8188b36c44d17784c5551f63accc5deaf8786f9d0ad1ae3cd8d887cbab4f777286dbb315fb14854c8774dc0d10b5567e4a705536cc2a1d61ec0a16a7a6 |
The quick brown fox jumps over the lazy dog | d135bb84d0439dbac432247ee573a23ea7d3c9deb2a968eb31d47c4fb45f1ef4422d6c531b5b9bd6f449ebcc449ea94d0a8f05f62130fda612da53c79659f609 |
FAQs
1. Can SHA-3 be decrypted?
No, SHA-3 is a one-way hash function, meaning it cannot be reversed or decrypted. Unlike encryption algorithms that allow for decryption with a key, hash functions like SHA-3 only generate fixed-length outputs with no way to retrieve the original data.
2. Is SHA-3 more secure than SHA-2 family?
SHA-3 serves as a modern, structurally distinct alternative to SHA-2, designed as a backup in case vulnerabilities emerged in SHA-2. While both are currently secure, SHA-3’s sponge-based Keccak algorithm eliminates SHA-2’s theoretical weaknesses (like length-extension attacks) and offers quantum-resistant design, making it ideal for future-proofing high-stakes systems.








