Need to generate SHA-256 hashes quickly? Our SHA-256 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
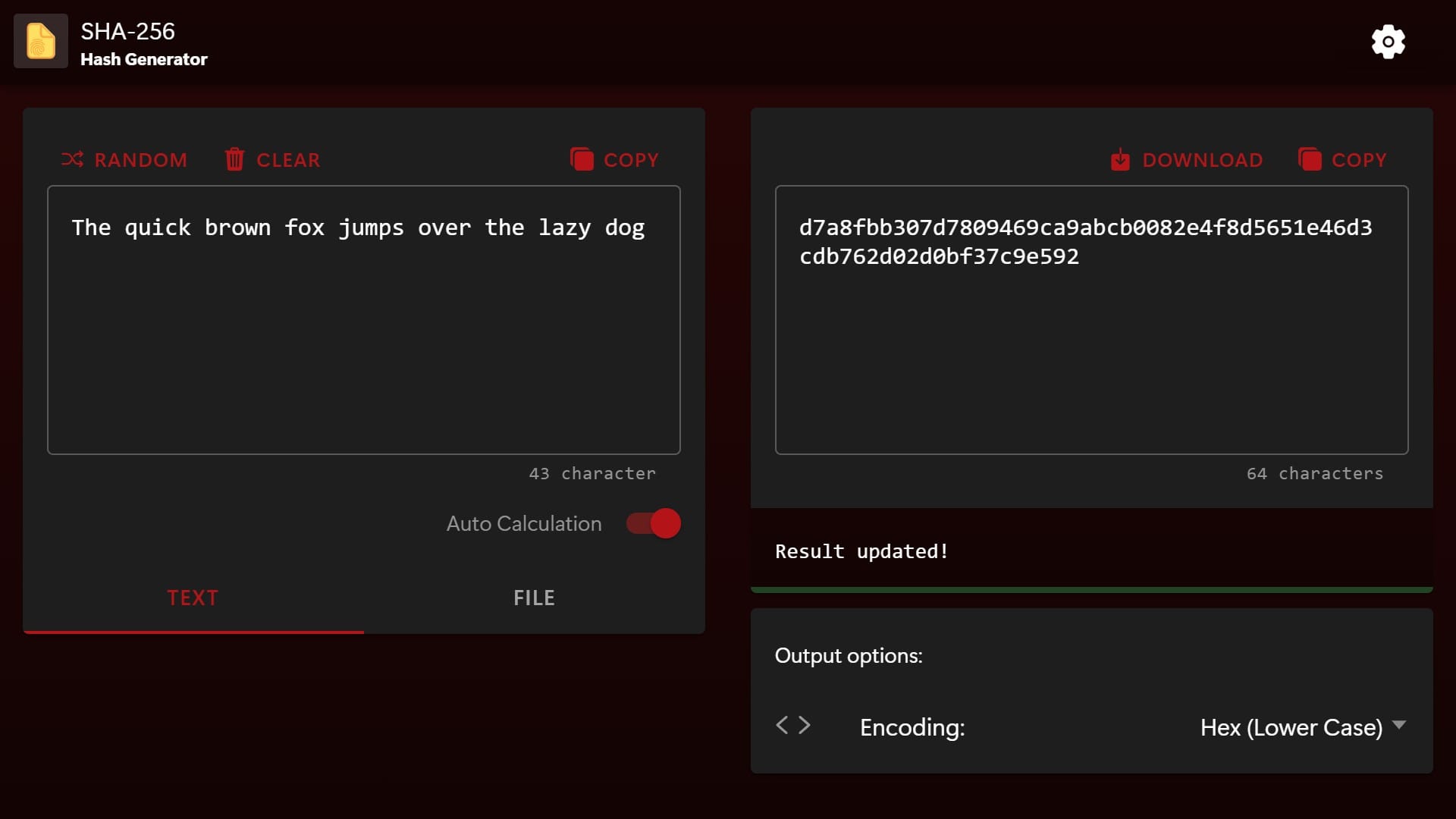
SHA-256 is part of the SHA-2 family, designed as a successor to SHA-1 with enhanced security against collision and preimage attacks. We will explain how they work and the steps to use them effectively. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
What is SHA-256?
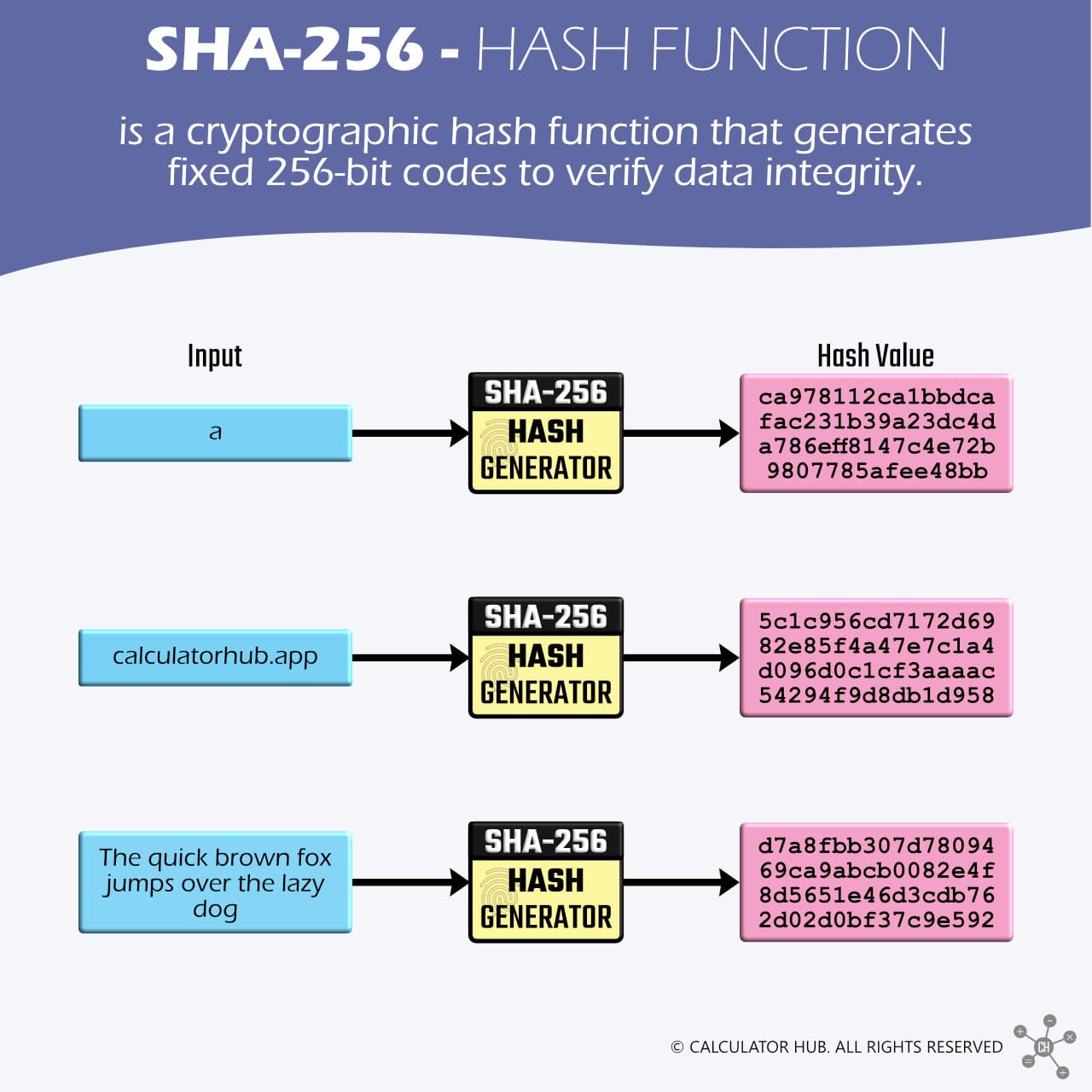
The Secure Hash Algorithm 256-bit (SHA-256) is a cryptographic hash function that produces fixed 256-bit codes to verify data integrity. Developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 2001[1], it is a member of the SHA-2 family, designed to replace SHA-1 and enhance security against collision and preimage attacks. SHA-256 processes data of any length, such as documents, text strings, or digital files, and converts it into unique alphanumeric sequences.
SHA-256 gained popularity due to its robust cryptographic resistance, making it a preferred choice for blockchain technology, digital signatures, password hashing, and secure data verification. Its design effectively addresses vulnerabilities found in older hash functions while remaining efficient for modern applications. The foundational principles of SHA-256 play a crucial role in cybersecurity, cryptographic protocols, and data protection today.
Key Features
Here are the key features of the SHA-256 cryptographic hash function.
- Fixed 256-bit Output: Regardless of input size, SHA-256 always generates a 256-bit hash, making it more secure than SHA-1's 160-bit output.
- Stronger Collision Resistance: SHA-256 significantly reduces the risk of hash collisions, meaning two different inputs are highly unlikely to produce the same hash value.
- One-Way Function: It is computationally infeasible to reverse SHA-256 and reconstruct the original input from its hash.
- Avalanche Effect: A minor modification in the input leads to a drastically different output, ensuring data integrity and security.
- Block-Based Processing: SHA-256 processes data in 512-bit blocks using complex transformations like bitwise shifts, modular additions, and logical functions to enhance security.
- Widely Used in Cryptography: SHA-256 is the backbone of blockchain security, digital signatures, password hashing, and certificate authentication, making it essential in modern cybersecurity.
Examples
Here are some real-life examples of how developers and systems have utilized SHA-256 in various situations.
Uses of SHA-256 in File Integrity Verification
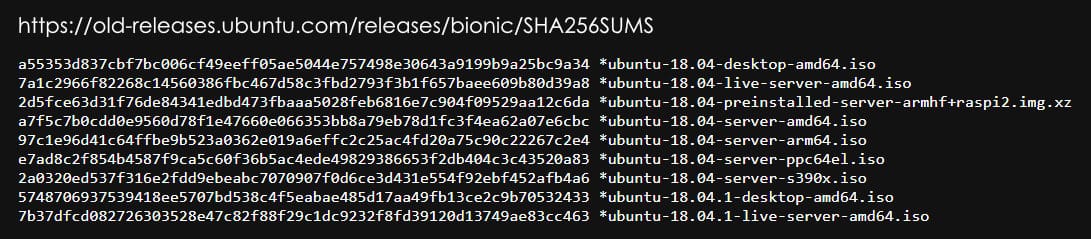
Linux OS downloads often include SHA-256 checksums so users can confirm ISO files match the original. Here is an example of SHA-256 checksums for Ubuntu ISO images that you can find at https://old-releases.ubuntu.com/releases/bionic/SHA256SUMS
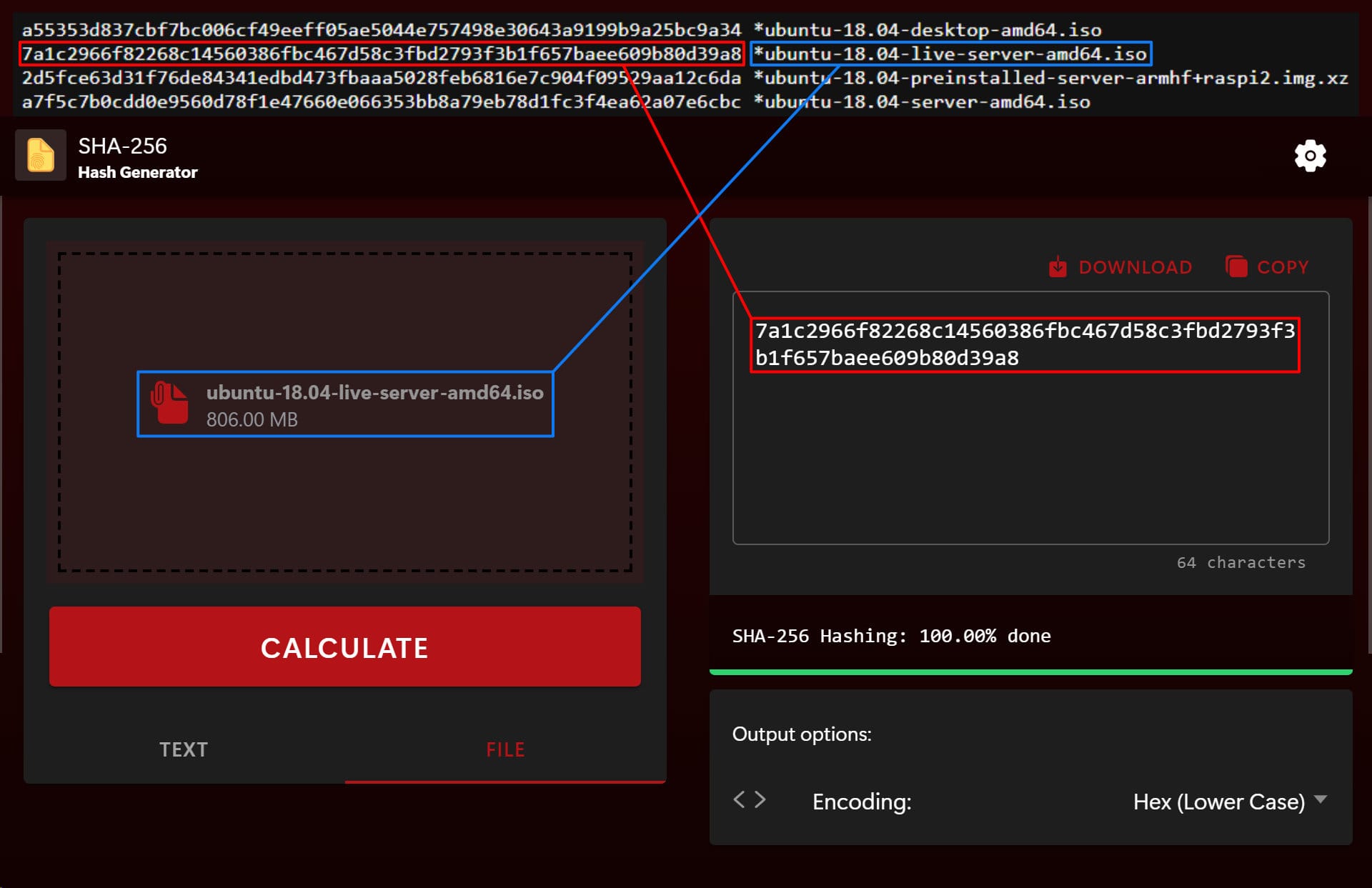
To demonstrate how to use our SHA-256 Hash Generator, I will download the ISO file named "ubuntu-18.04-live-server-amd64.iso" and verify that it has downloaded correctly.
First, I will navigate to the File tab, select the downloaded ISO file, and click "Calculate" to generate its hash value. This process may take a few minutes, depending on the speed of your computer.
Once the calculation is complete, I will compare the hash result from our generator with the SHA-256 checksum provided on the official website. As you can see, the hash values match.