Need to generate SHA-224 hashes quickly? Our SHA-224 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
SHA-224 is part of the SHA-2 family (think: SHA-256’s sibling) and works almost the same way. However, it spits out a shorter 224-bit code instead of a 256-bit code. It’s designed for situations where you need a smaller "digital fingerprint" but still want strong security. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
What is SHA-224?
SHA-224, a member of the SHA-2 family, creates 56-character codes (224 bits) to confirm data hasn’t been altered. Designed by the NSA and formalized by NIST in 2001[1], it serves as a shorter variant of SHA-256, ideal for scenarios where space matters but security can’t be compromised. Whether handling text, files, or other digital inputs, it distills them into unique fingerprints using a mix of letters and numbers.
Initially tailored for systems requiring efficient hash sizes, such as older hardware or constrained environments, it balances brevity with the SHA-2 family’s robust safeguards. While less common than its 256-bit counterpart, SHA-224 still supports niche uses, such as verifying software updates or securing low-resource devices. Its design principles, rooted in irreversible scrambling of data, help maintain trust in applications like tamper-proof logs or lightweight authentication. Despite being overshadowed by newer algorithms, it persists in legacy systems where its balance of size and security remains practical.
Key Features
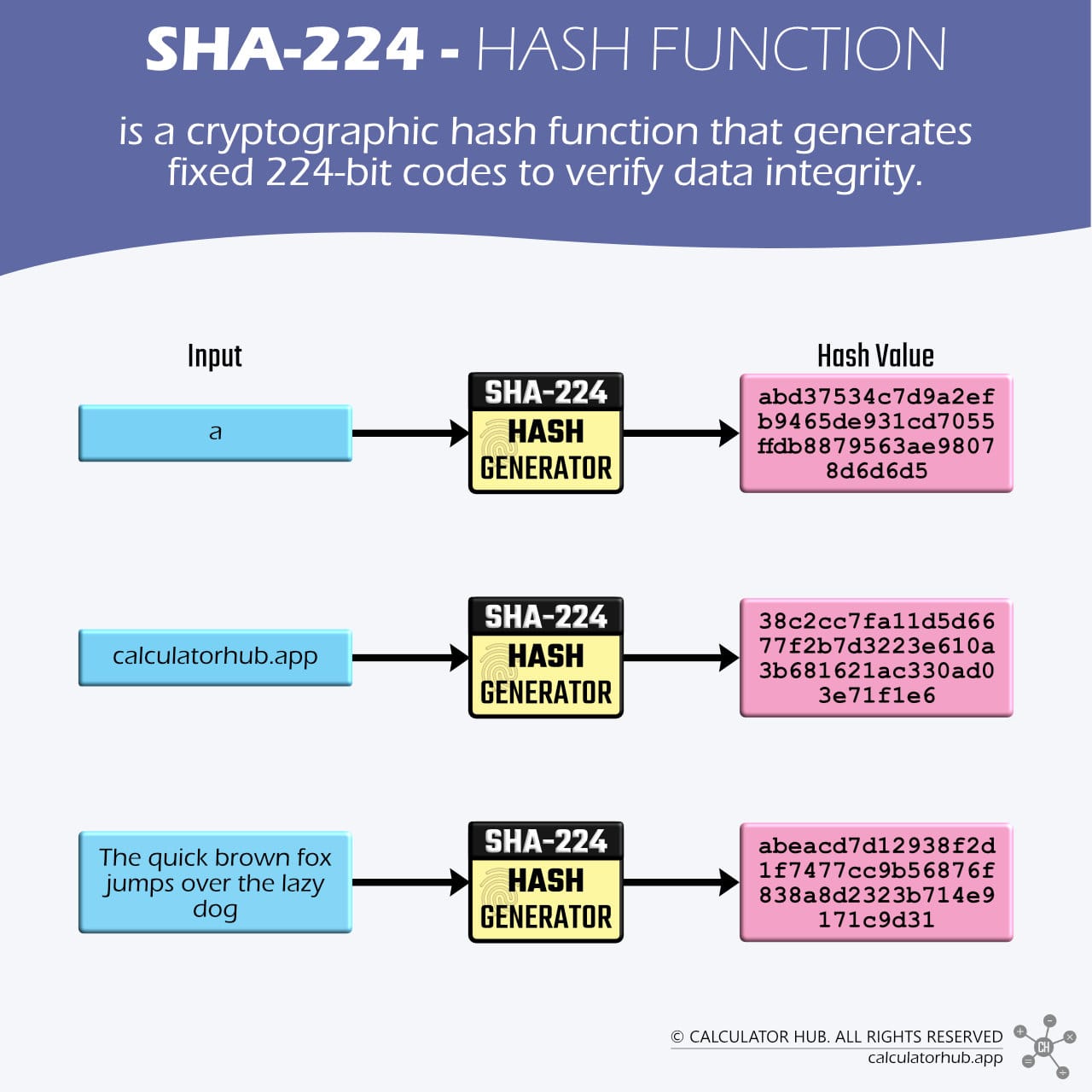
Here are the key features of the SHA-224 cryptographic hash function.
- Fixed 224-Bit Output: Regardless of input size, SHA-224 always produces a 224-bit hash, making it a more compact alternative to SHA-256 while maintaining strong cryptographic security.
- Strong Collision Resistance: SHA-224 reduces the likelihood of two different inputs generating the same hash, offering better collision resistance than SHA-1.
- One-Way Function: It is computationally infeasible to reverse the hash and retrieve the original input, ensuring strong data protection.
- Avalanche Effect: Even the smallest change in the input completely alters the hash, reinforcing data integrity and security.
- Optimized for Efficiency: With a shorter hash length than SHA-256, SHA-224 is useful for systems requiring faster processing and lower storage needs while still maintaining security.
- Block-Based Processing: SHA-224 processes data in 512-bit blocks, applying multiple logical operations, bitwise shifts, and modular additions for enhanced hash strength.
- Used in Digital Signatures & Authentication: SHA-224 supports cryptographic applications such as digital signatures, secure authentication protocols, and integrity verification where smaller hash sizes are preferred.
Examples
Here’s a table of text samples along with their corresponding SHA-224 hash values:
| Text Input | SHA-224 Hash Output |
|---|---|
Apple | 476432a3e85a0aa21c23f5abd2975a89b6820d63 |
Blackberry | 9d804384027293627da4592b0977bf39476727bf |
The quick brown fox jumps over the lazy dog | 2fd4e1c67a2d28fced849ee1bb76e7391b93eb12 |
FAQs
1. Can SHA-224 be "decrypted"?
No, SHA-224 is a one-way hash function, meaning it cannot be reversed or decrypted. Unlike encryption algorithms that allow for decryption with a key, hash functions like SHA-224 only generate fixed-length outputs with no way to retrieve the original data.
2. Is SHA-224 safer than SHA-1?
Absolutely. SHA-224, despite its shorter hash, is far safer than the outdated SHA-1. It shares SHA-256’s reinforced design, making intentional hash collisions (creating two inputs with the same output) astronomically harder. It’s the difference between breaking into a shed versus a bank vault.
3. What are practical use cases for SHA-224?
SHA-224 is typically deployed in scenarios requiring SHA-2 security with minimal storage overhead:
- Legacy hardware: Older embedded systems, IoT devices, or low-power chips with limited memory.
- Regulatory compliance: Industries bound by standards mandating fixed hash lengths (e.g., some government or financial protocols).
- Digital signatures: Lightweight certificate schemes where shorter hashes reduce computational load.
4. How does SHA-224 differ from SHA-256?
SHA-224 and SHA-256 share identical core algorithms, but SHA-224 produces a shorter 224-bit output (56 hexadecimal characters) compared to SHA-256’s 256-bit output. They also use distinct initial numerical values (initialization constants) during computation, which alters the starting state of the hashing process. The truncation of the final output makes SHA-224 more storage-efficient for specific applications.








