Need to generate SHA-1 hashes quickly? Our SHA-1 hash generator lets you create them by typing text or selecting files. It’s a straightforward way to check information accuracy or confirm files haven’t been altered.
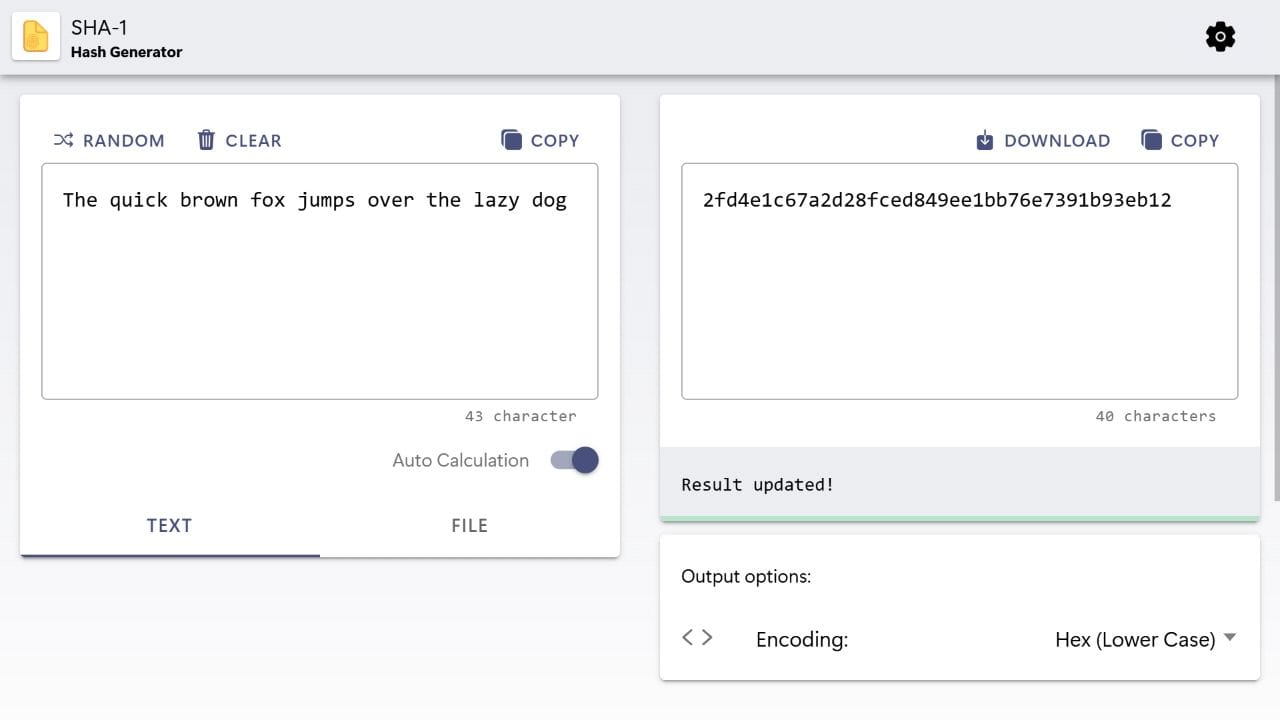
SHA-1 hashes act like digital fingerprints to verify information. We will explain how they work and the steps to use them effectively. You’ll also find basic terms, practical examples, and answers to common questions to understand further.
Definitions
What is SHA-1?
SHA-1, short for Secure Hash Algorithm 1 is a cryptographic hash function that generates fixed 160-bit codes to verify data integrity. Developed by the National Security Agency (NSA)[1] and published by the National Institute of Standards and Technology (NIST) in 1995, SHA-1 processes data of any length, including documents, text strings, or digital files, and transforms them into distinct alphanumeric sequences.
Initially, SHA-1 was valued for its reliability in cryptographic applications, including digital signatures and file integrity verification. However, as advancements in security research exposed vulnerabilities, especially collision attacks, SHA-1 was gradually phased out in favor of stronger hashing algorithms such as SHA-256. Despite its weaknesses, SHA-1’s foundational principles remain relevant in discussions about hash functions and data security today.
Key Features of SHA-1
Here are the key features of the SHA-1 cryptographic hash function.
- Fixed 160-Bit Output: No matter the input size, SHA-1 always generates a 160-bit hash, ensuring consistency in data fingerprinting.
- One-Way Function: Like MD5, SHA-1 is irreversible, meaning the original input cannot be reconstructed from the hash.
- Input Sensitivity: Even the smallest change in input data produces a vastly different hash, demonstrating the "avalanche effect."[2]
- Moderate Speed: While SHA-1 is slightly slower than MD5 due to its more complex operations, it was once favored for secure file verification and digital signatures.
- Block-Based Processing: SHA-1 breaks input data into 512-bit blocks and processes them in multiple rounds, refining the output to ensure unique hash generation.
- Widespread Legacy Use: Although it is now considered insecure for cryptographic purposes, SHA-1 was extensively used in digital certificates, file integrity verification, and version control systems like Git.
Examples
Here are some real-life examples of how developers and systems have utilized SHA-1 in various situations.
Uses of SHA-1 in File Integrity Verification
Linux OS downloads often include SHA-1 checksums so users can confirm ISO files match the original. Here is an example of SHA-1 checksums for Ubuntu ISO images that you can find at https://old-releases.ubuntu.com/releases/bionic/SHA1SUMS
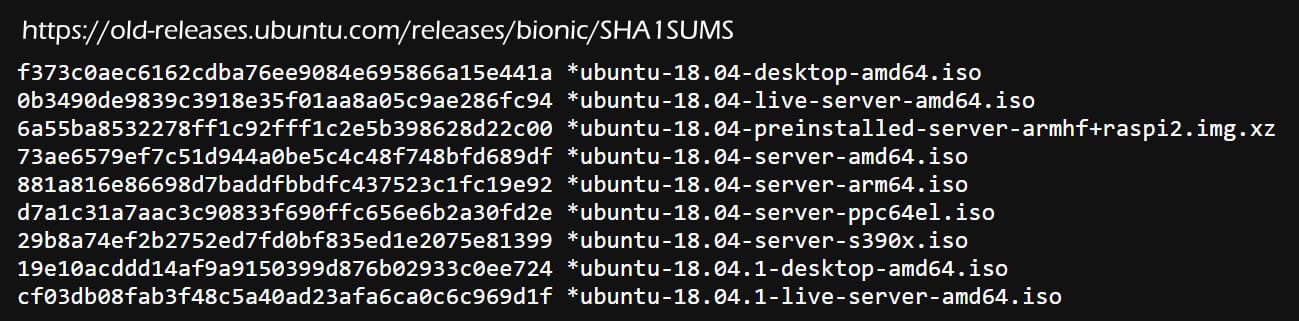
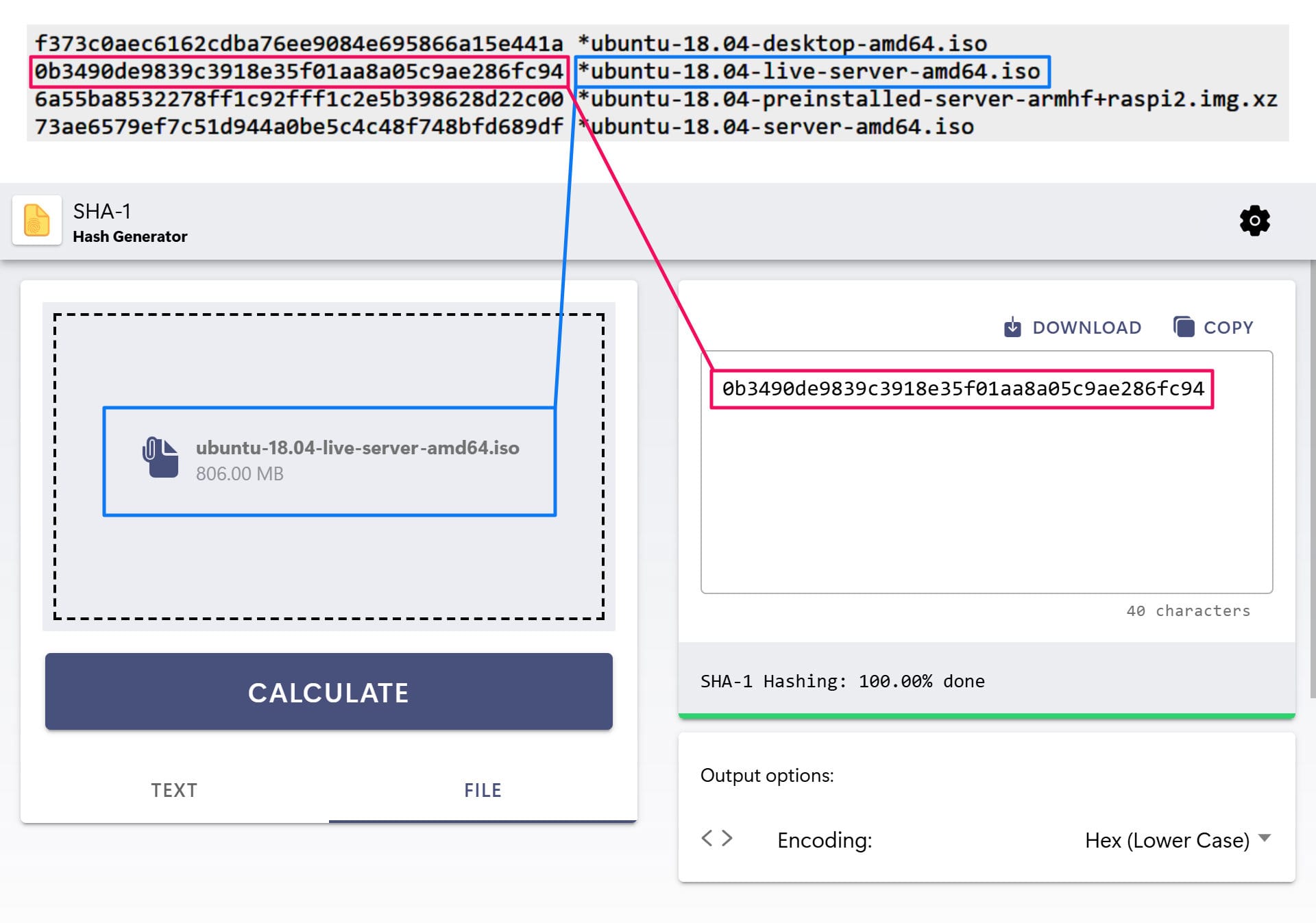
To demonstrate how to use our SHA-1 Hash Generator, I will download the ISO file named "ubuntu-18.04-live-server-amd64.iso" and verify that it has downloaded correctly.
First, I will navigate to the File tab, select the downloaded ISO file, and click "Calculate" to generate its hash value. This process may take a few minutes, depending on the speed of your computer.
Once the calculation is complete, I will compare the hash result from our generator with the SHA-1 checksum provided on the official website. As you can see, the hash values match.
How SHA-1 Works
SHA-1 is a cryptographic hash function designed to process input data and produce a fixed 160-bit hash. The process follows five fundamental stages: padding, message expansion, iterative compression, state updates, and final hash generation.
Step 1: Padding the Input
SHA-1 processes data in 512-bit blocks, meaning an input must be adjusted to fit this structure. If the message length is insufficient, it undergoes padding:
- A '1' bit is appended first.
- '0' bits follow until the message length reaches 448 bits modulo 512.
- The final 64 bits contain the original message length in binary, ensuring the total length aligns with SHA-1’s block requirements.
Step 2: Message Expansion
After padding, the data is divided into 512-bit blocks, each further split into 16 words of 32 bits. These words are expanded into 80 words using bitwise operations and shifts, creating additional complexity in the hash calculation.
Step 3: Iterative Compression
SHA-1 employs five 32-bit registers initialized with specific constants:
- A = 0x67452301
- B = 0xEFCDAB89
- C = 0x98BADCFE
- D = 0x10325476
- E = 0xC3D2E1F0
Each message block undergoes 80 rounds of processing, divided into four distinct functions:
- Rounds 1-20: A logical function combining AND, OR, NOT operations.
- Rounds 21-40: XOR-based transformations.
- Rounds 41-60: A mix of AND and OR operations.
- Rounds 61-80: Further XOR transformations.
Each round applies predefined constants and modular arithmetic to manipulate the registers.
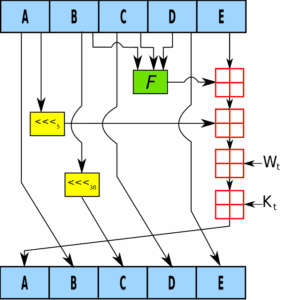
Source: Wikipedia.org
Step 4: Updating the State
Throughout each iteration, SHA-1 updates the five registers, progressively refining the intermediate hash value. This step ensures that even a minimal change in input significantly alters the output due to SHA-1’s avalanche effect.
Step 5: Producing the Final Hash
Once all blocks are processed, the final 160-bit hash is created by concatenating the five 32-bit register values:
SHA-1 Digest = A B C D E
FAQs
1. What are the common use cases of the SHA-1 Hash Generator?
SHA-1 hash generator is widely used for everyday tasks in verification workflows. Here’s where they’re most often applied:
- Digital Signatures & Certificates: SHA-1 was once the backbone of SSL/TLS certificates, which verified websites’ identities. Companies like Certificate Authorities (CAs) used SHA-1 to create these certificates, which helped browsers and websites communicate securely. However, after flaws were found, browsers like Chrome and Firefox replaced SHA-1 certificates entirely, switching to SHA-256.
- Checking File Integrity
Developers used SHA-1 to confirm downloaded software (like Linux installers) wasn’t tampered with. Projects shared SHA-1 checksums so users could compare them to downloaded files. You can think of it as a “receipt” to prove nothing was altered. - Version Control (Git): Git uses SHA-1 to tag every commit, file, and folder in a project’s history. These unique IDs let developers track changes reliably. However, because SHA-1 collisions could break this trust, Git is slowly moving to safer alternatives.
- Password Storage (Now Outdated): Years ago, some systems stored passwords as SHA-1 hashes. While this wasn’t secure (hackers can crack it easily), it was better than plain text. Modern apps now use stronger tools like bcrypt or SHA-256 to scramble passwords.
- Digital Rights Management (DRM): SHA-1 helped DRM systems verify media files (like movies or music) to block piracy. It ensured files weren’t altered illegally, though newer methods have replaced it.
- Secure Boot & Firmware Checks: Older devices used SHA-1 to validate firmware during startup, ensuring no malicious code was loaded. Today, SHA-2 handles this role, as SHA-1 isn’t trustworthy for high-security tasks.
2. Why did SHA-1 stick around longer than MD5 before being phased out?
SHA-1 was tougher to crack than MD5, so it stayed useful for website certificates and tracking code changes in systems like Git. Even after flaws were known, nobody rushed to replace them because updating old systems is a pain. It wasn’t until researchers proved hackers could exploit it (like creating fake matching hashes) that the tech world finally ditched it.
3. Is SHA-1 useless now?
Not entirely! If security isn’t your priority, SHA-1 still works for jobs like:
- Finding duplicate files (e.g., cleaning up your messy cloud storage).
- Basic checksums to catch accidental file corruption.
- Tagging data for quick lookups in databases.
- Just don’t use it for anything a hacker might care about.
4. When did SHA-1’s flaws get exposed in the real world?
In 2017, Google and CWI Amsterdam publicly showcased the first practical collision attack on SHA-1, demonstrating how two different PDFs can share the same SHA-1 hash.[3].








